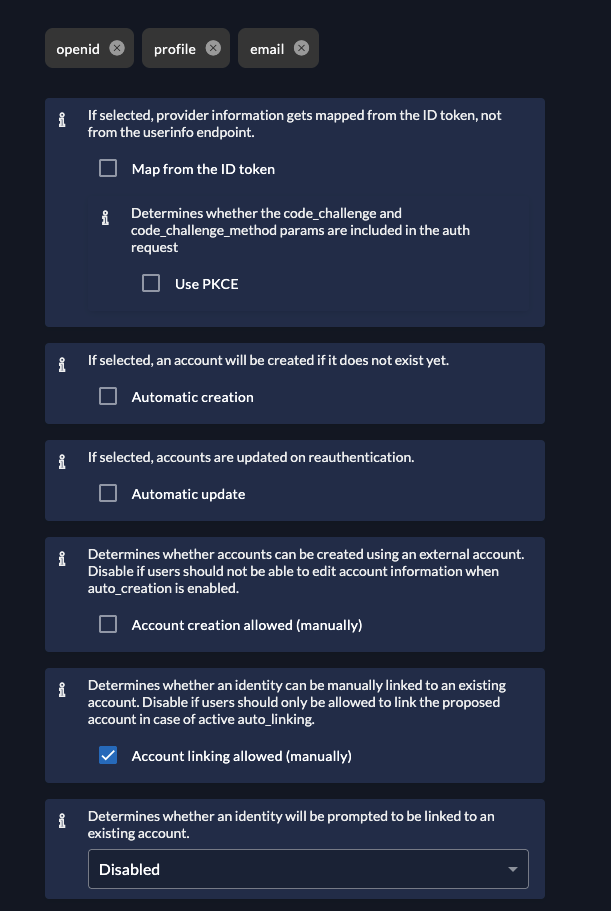
Custom UI
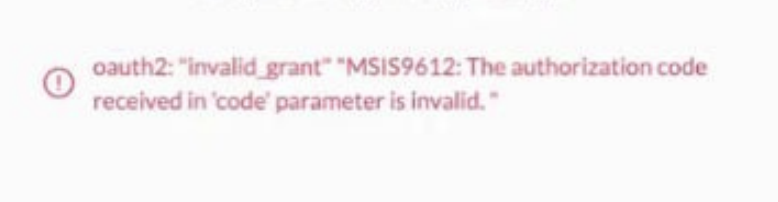
Azure Active Directory IDP / Invalid grant_type MSIS 9612
[Bug] Zitadel Chart - v2 login 'wait-for-zitadel' fails with service mesh (linkerd) K8S
Build image and push to ECR
Zitadel v2beta API – ListOrganizationMetadata returns 404
Scoping to specific organization in JWT token
Best practice to copy user id from Zitadel DB my App DB?
Trouble adding IAMMember (aka Administrator)
Import human users with the v2 API not working as expected
/management/v1/users/human/_import works as expected and the user receives an initialization email if the email address is not marked as verified or if no password is set.
...Initial User not supported
ghcr.io/zitadel/zitadel:latest) using the start-from-init command and setting all relevant ZITADEL_FIRSTINSTANCE_* environment variables.
Here’s what works:...Logon issues with 4.3.2
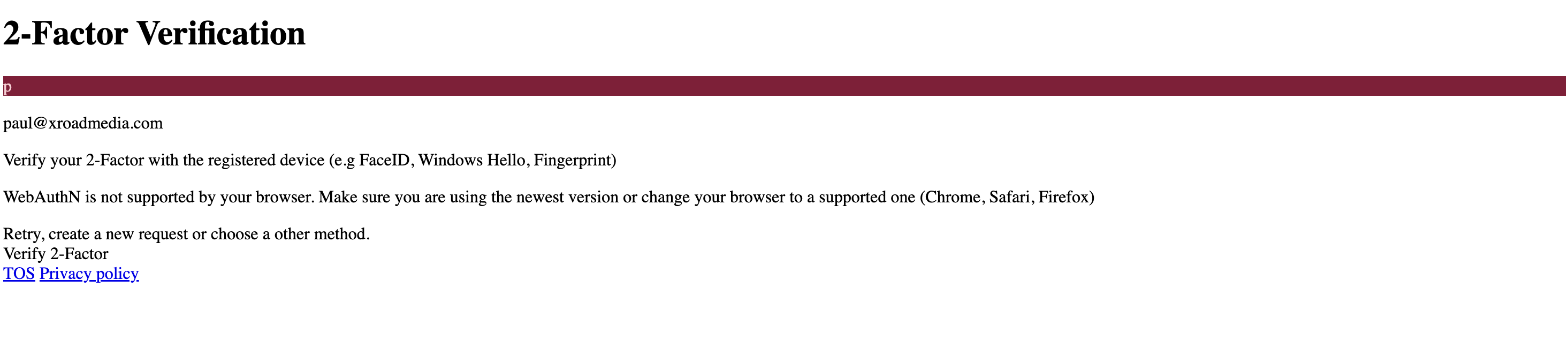
v4.3.2 missing binaries?
v4.3.2 breaks CSS
Passwordless authentication with email OTP
Are there any plans to update the Zitadel .NET SDK to use the latest API changes?
OTP Mail not sent
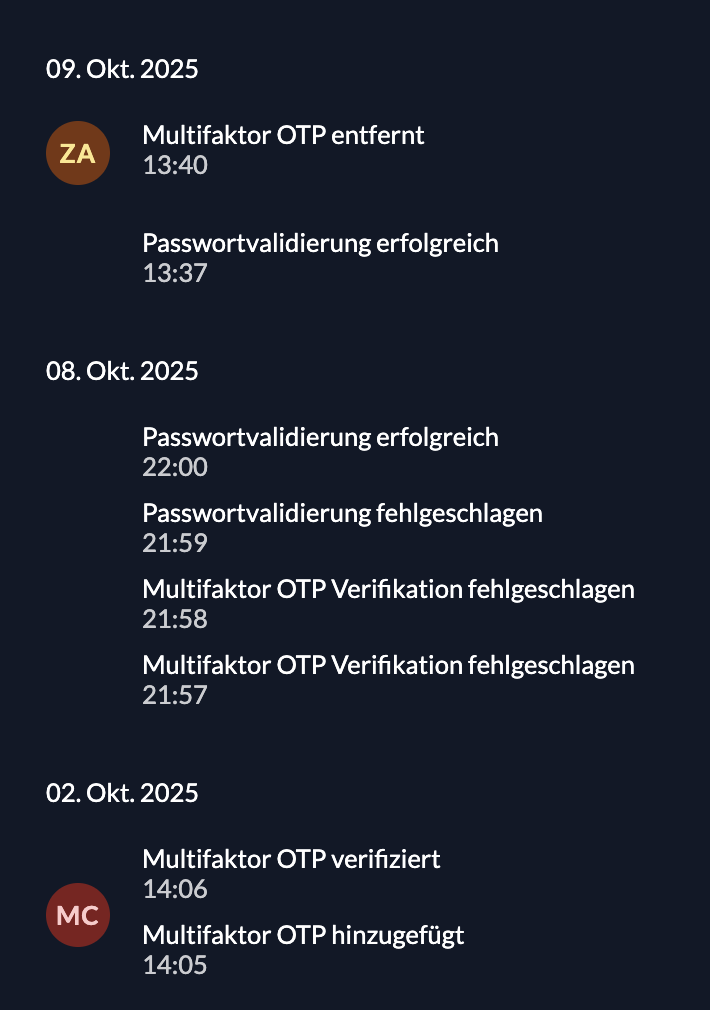
upgrading from v2.65.10 to v2.66.0 error at setup
Getting authRequestID v1 instead of authRequestId v2. Due to which createCallbackUrl API is failing.
Reset password with code not working