MFA vs 2FA lifetimes
⚙️Configuration🏬Self-hosted🔍Authentication❓Question✅Solved
MFA Descriptions:
https://zitadel.com/docs/guides/manage/console/default-settings#multifactor-mfa
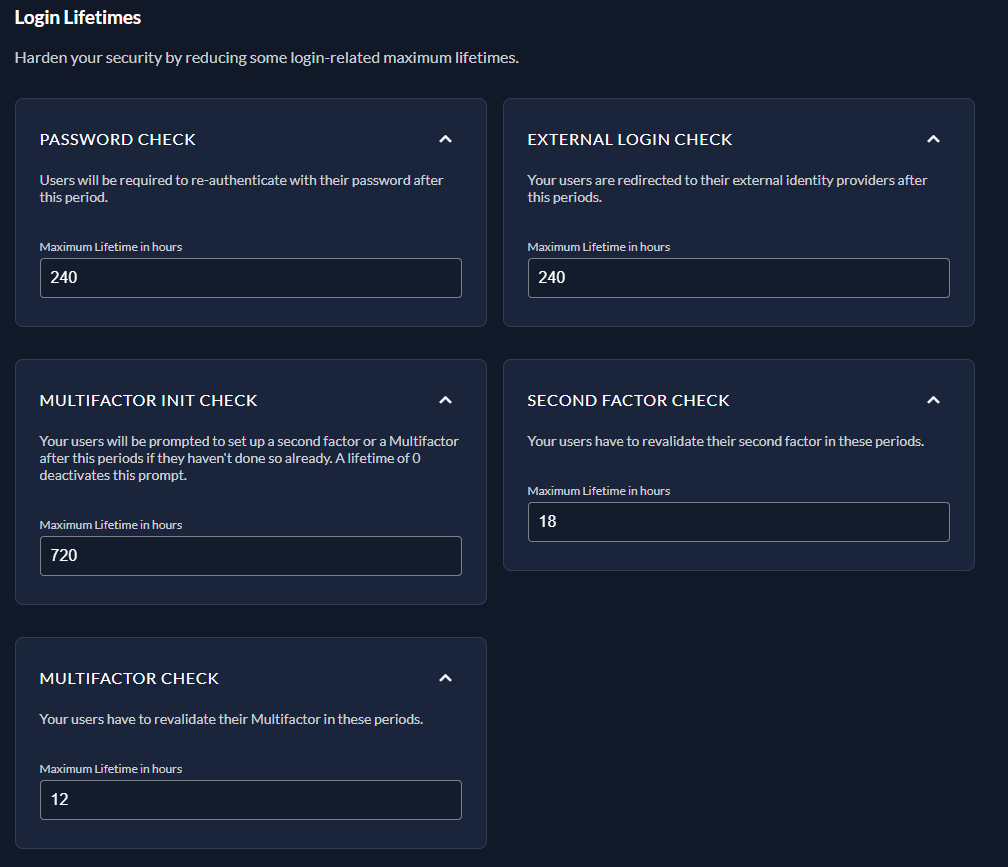
Login Lifetimes:
https://zitadel.com/docs/guides/manage/console/default-settings#login-lifetimes
Detail Information on Lifetimes:
https://zitadel.com/docs/apis/resources/settings_service_v2/settings-service-get-login-settings
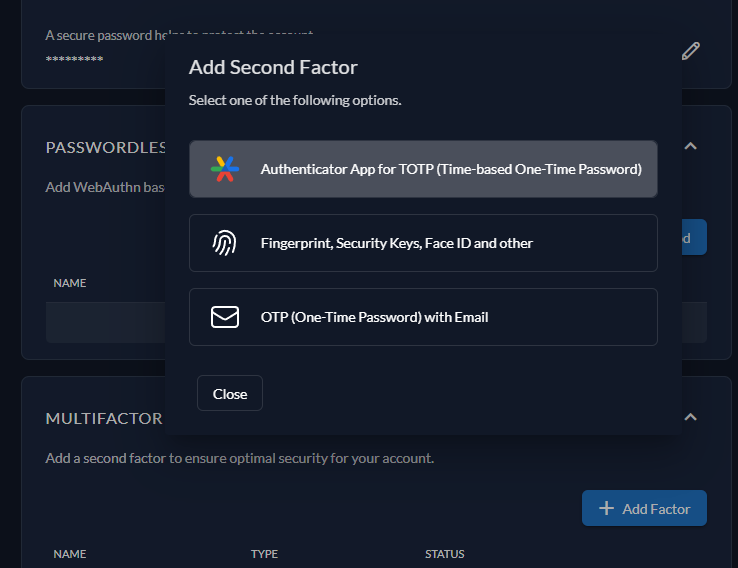
I'm trying to determine the difference between the "Second Factor Check" and "Multifactor Check" and how I can know when one timer is being used for a given login.
When you look at a users settings, all of the second factors are within the MFA? Yet, when I go to the API designations I see different things.
So if someone is using a U2F, is this a secondaryFactor of multiFactor?
-
-
https://zitadel.com/docs/guides/manage/console/default-settings#multifactor-mfa
Login Lifetimes:
https://zitadel.com/docs/guides/manage/console/default-settings#login-lifetimes
Detail Information on Lifetimes:
https://zitadel.com/docs/apis/resources/settings_service_v2/settings-service-get-login-settings
I'm trying to determine the difference between the "Second Factor Check" and "Multifactor Check" and how I can know when one timer is being used for a given login.
When you look at a users settings, all of the second factors are within the MFA? Yet, when I go to the API designations I see different things.
So if someone is using a U2F, is this a secondaryFactor of multiFactor?
-
secondFactors - SECOND_FACTOR_TYPE_U2F-
multiFactors - MULTI_FACTOR_TYPE_U2F_WITH_VERIFICATION