client_credentials issue
1) My company is switching to a new authorisation server selected server is Zitadel
2) Self hosting
3) 4.4.0
4) Nothing fancy java spring boot 3.3.0 Docker latest (4.48.0) postman if that is even important here
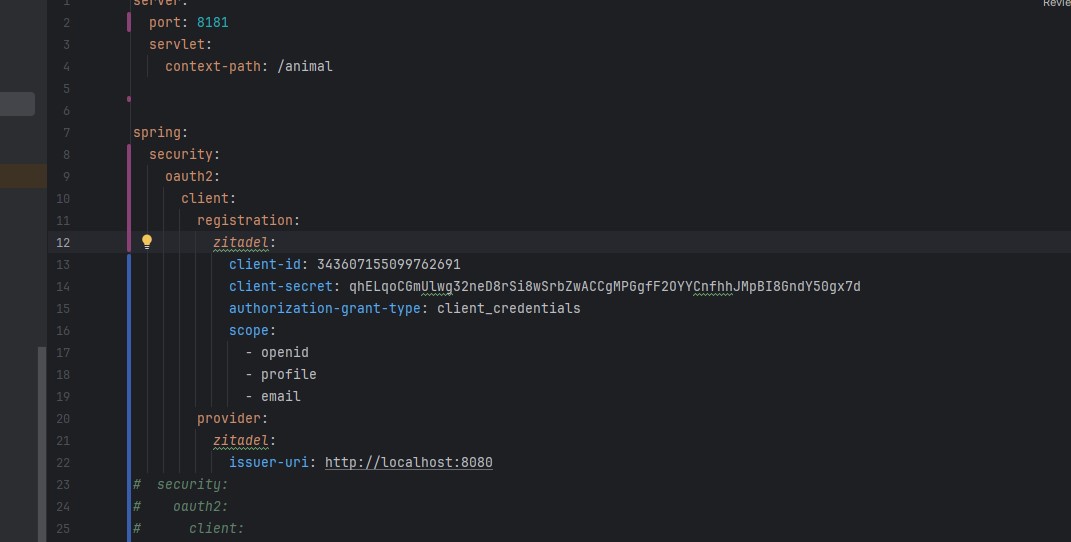
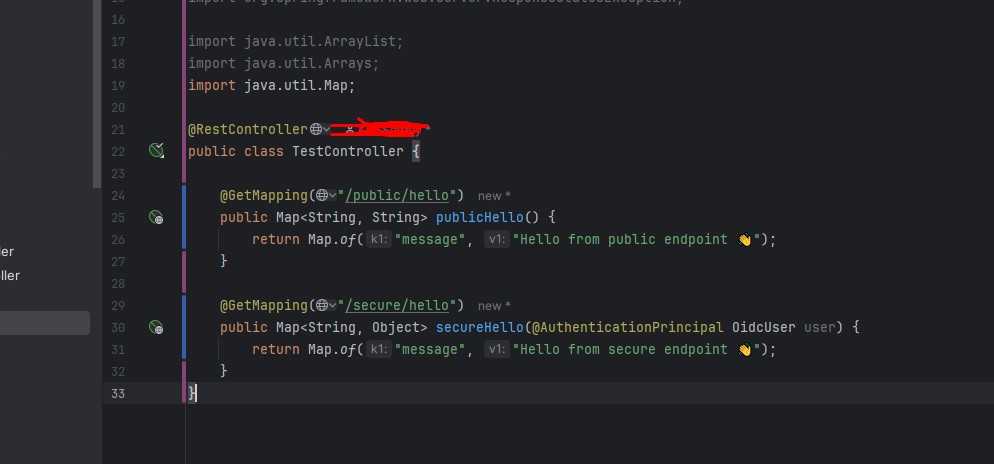
5-6) Ok so i'm trying to create a client_credentials connection, i set my spring to a certain client screenshot 1, and i'm trying to access the general dummy method public one works flawlessly secure one? not so much.
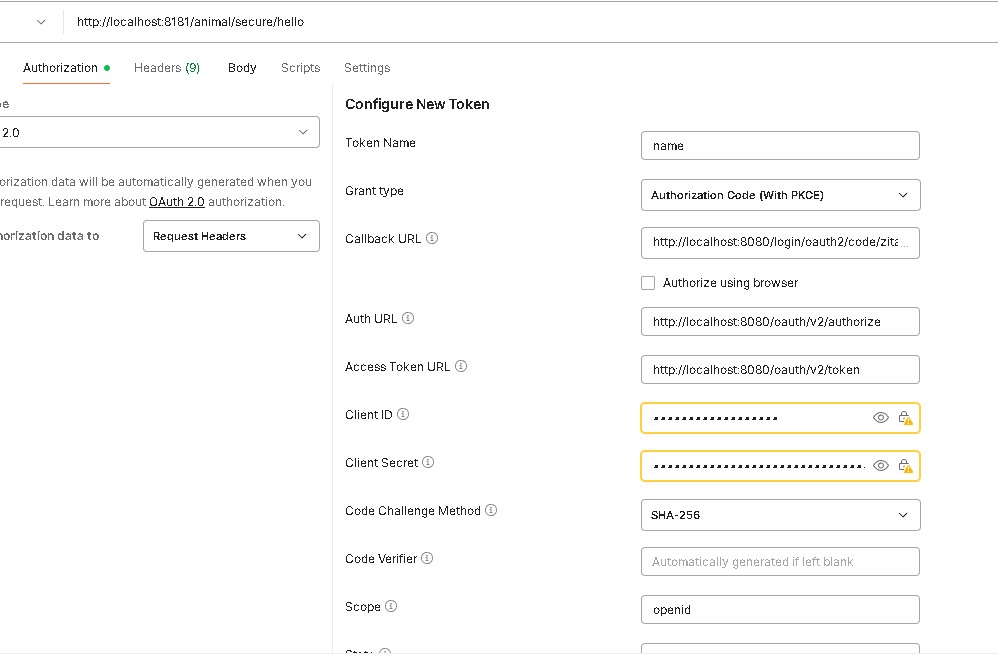
i set all the right credentials right links and It works, i get the token use it as a bearer, yet nothing happens, when i try to send a request i get redirected to the login form even tho i have a bearer token. But the bigger offender is when i swap grant type from authorisation code to the client credentials and yes i hear you i added an app within zitadel that has type API and sent it's credentials (both as basic with grant type cllient_credentials and as client_credentials neither worked) and it just s says in docker:
time=2025-10-29T12:07:32.575Z level=WARN msg="request error" oidc_error.parent="ID=QUERY-Dfbg2 Message=Errors.User.NotFound Parent=(sql: no rows in result set)" oidc_error.description="client not found" oidc_error.type=invalid_client status_code=400
and in postman
Error: invalid_client, Description: client not found
help me plz. i need it to work as client_cedentials or password credentials. no login form machine to machine. THX in advance
2) Self hosting
3) 4.4.0
4) Nothing fancy java spring boot 3.3.0 Docker latest (4.48.0) postman if that is even important here
5-6) Ok so i'm trying to create a client_credentials connection, i set my spring to a certain client screenshot 1, and i'm trying to access the general dummy method public one works flawlessly secure one? not so much.
i set all the right credentials right links and It works, i get the token use it as a bearer, yet nothing happens, when i try to send a request i get redirected to the login form even tho i have a bearer token. But the bigger offender is when i swap grant type from authorisation code to the client credentials and yes i hear you i added an app within zitadel that has type API and sent it's credentials (both as basic with grant type cllient_credentials and as client_credentials neither worked) and it just s says in docker:
time=2025-10-29T12:07:32.575Z level=WARN msg="request error" oidc_error.parent="ID=QUERY-Dfbg2 Message=Errors.User.NotFound Parent=(sql: no rows in result set)" oidc_error.description="client not found" oidc_error.type=invalid_client status_code=400
and in postman
Error: invalid_client, Description: client not found
help me plz. i need it to work as client_cedentials or password credentials. no login form machine to machine. THX in advance