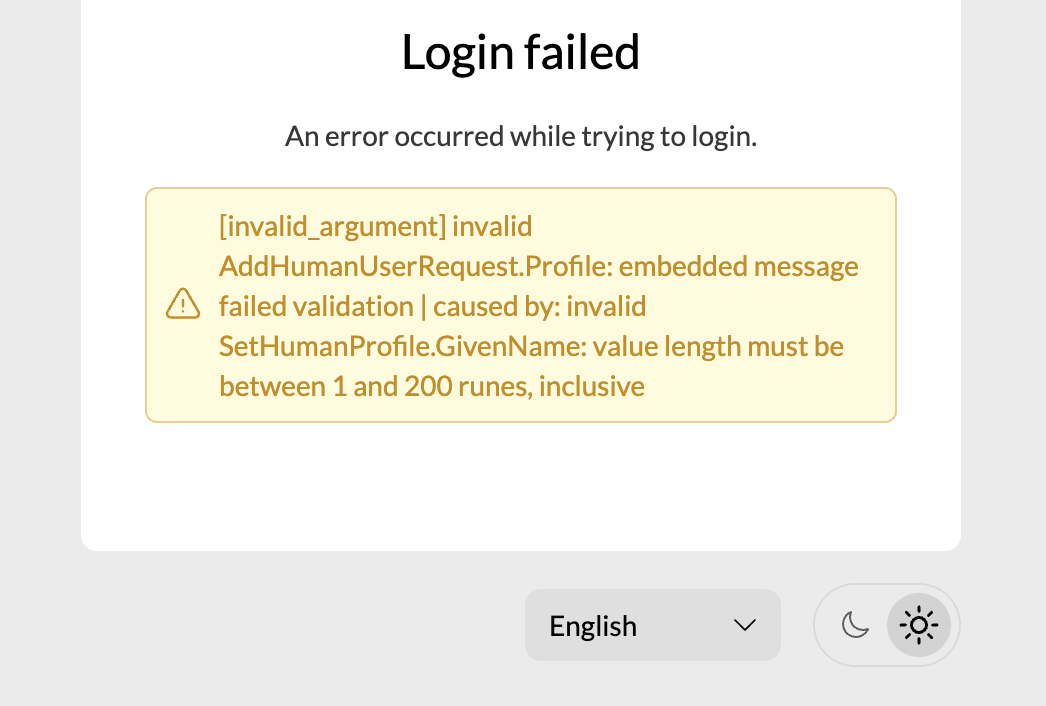
External OAuth2 provider Error:SetHumanProfile.GivenName: value length must be between 1 and 200 run
I use an external OAuth2 provider as an alternative to the default zitadel login. Currently im facing the following error after succesfull OAuth login flow:
"[invalid_argument] invalid AddHumanUserRequest.Profile: embedded message failed validation | caused by: invalid SetHumanProfile.GivenName: value length must be between 1 and 200 runes, inclusive"
Zitadel is requesting the OAuth2 user endpoint and getting the following example response:
Zitadel Settings:
- ID Attribute: "sub" (uuid is working as well)
- Scopes: "user:read"
Questions:
- Is there any example response in the docs where the correct userendpoint json structure is listed for the external OAuth2 IDP?
- Can anyone help how the "given_name" must me formatted?
Thank u so much
"[invalid_argument] invalid AddHumanUserRequest.Profile: embedded message failed validation | caused by: invalid SetHumanProfile.GivenName: value length must be between 1 and 200 runes, inclusive"
Zitadel is requesting the OAuth2 user endpoint and getting the following example response:
Zitadel Settings:
- ID Attribute: "sub" (uuid is working as well)
- Scopes: "user:read"
Questions:
- Is there any example response in the docs where the correct userendpoint json structure is listed for the external OAuth2 IDP?
- Can anyone help how the "given_name" must me formatted?
Thank u so much