Multiple bugs with Microsoft IdP
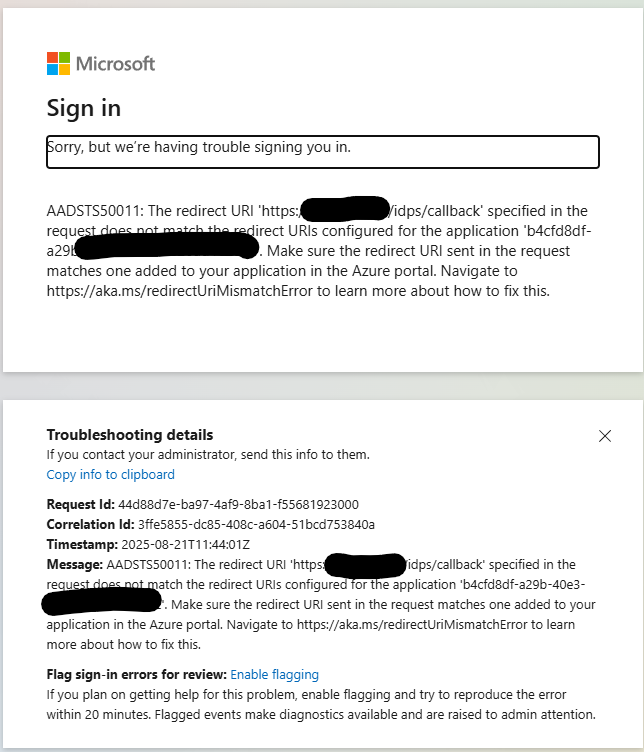
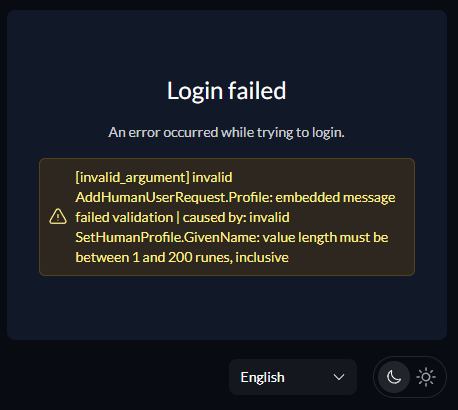
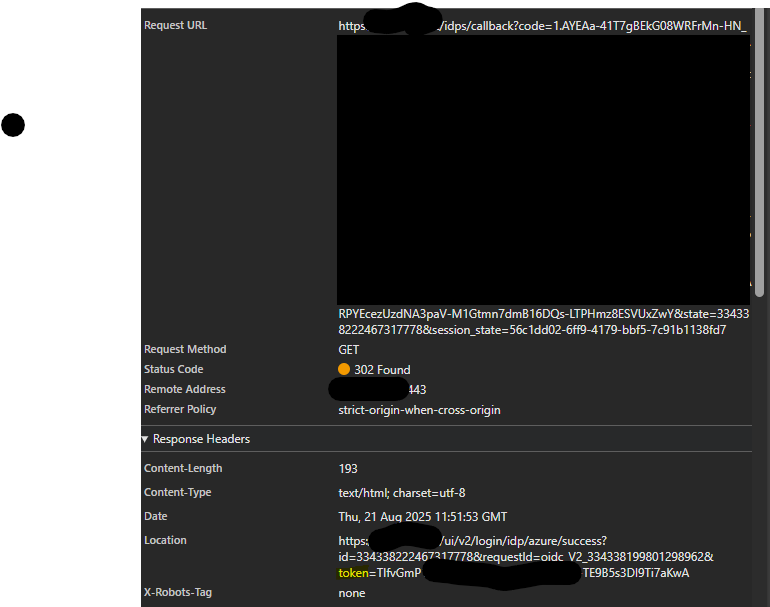
Hello there, I've tried to set up Microsoft IdP in the default settings on a fresh self-hosted instance of Zitadel version 4.0.2, but i encountered a lot of issues and I'm at a loss. I've followed every step in the documentation and, at first, the first error I get is from Microsoft (first image): the url provided by the registration page (/ui/login/login/externalidp/callback) doesn't match with what is actually requested (/ipds/callback). Adding it to the allowed redirect URIs in Entra let's me move only to get a Login failed error (second image). Following an older threat i've found here i tried to search for "id_token" in the network requests but didn't find anything, searching just for "token" i've found the callback request with the auth code but no cleartext jwt.
Can anyone help me?
Thanks so much in advance!
L.
Can anyone help me?

Thanks so much in advance!
L.