Microsoft IdP Login Fails: Missing given_name Causes Validation Error
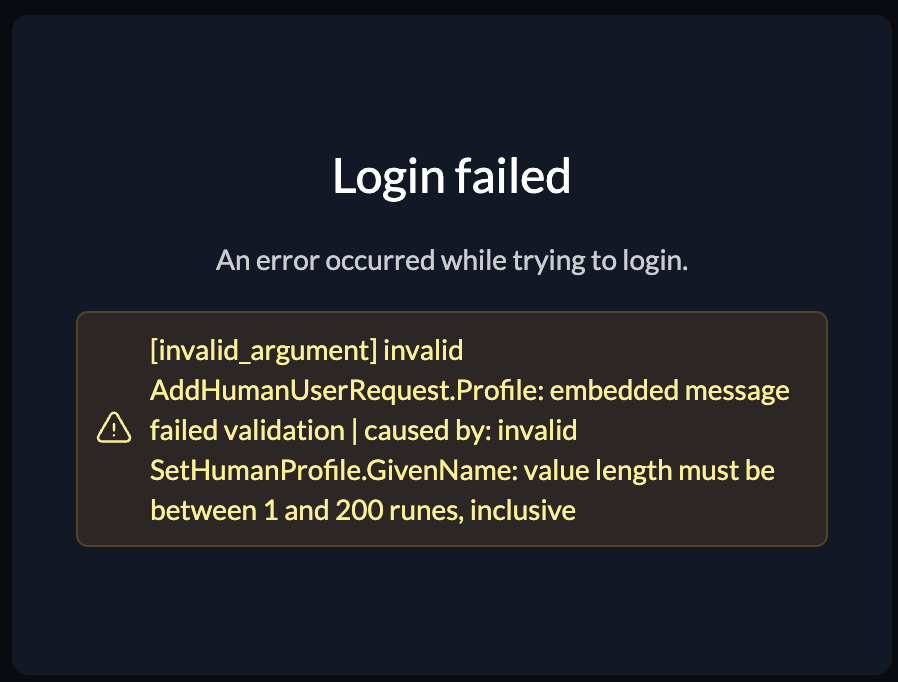
Hello, I'm setting up Microsoft as an Identity Provider for my app using Zitadel. I followed all the documentation, and login is successful, but right after that, I run into this error:
Even though I have added
Can anyone help me identify why this might be happening or suggest a workaround? maybe creating an action to map name to given_name can fix this (not sure if possible)?
Thanks so much in advance!
[invalid_argument] invalid AddHumanUserRequest.Profile: embedded message failed validation | caused by: invalid SetHumanProfile.GivenName: value length must be between 1 and 200 runes, inclusiveEven though I have added
given_nameCan anyone help me identify why this might be happening or suggest a workaround? maybe creating an action to map name to given_name can fix this (not sure if possible)?
Thanks so much in advance!