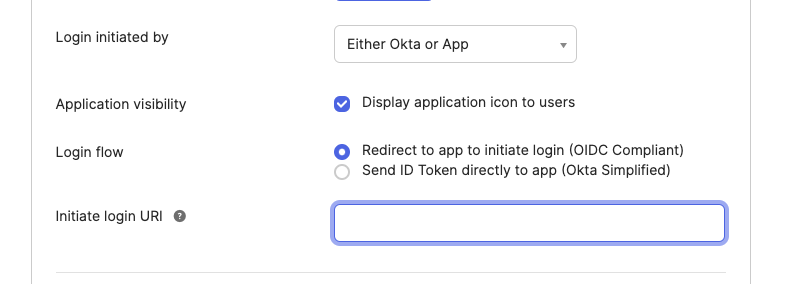
Initate Login URI from SSO provider
Hello, I have a client who is integrating with us using their okta oidc client. For the most part everything is working well, but we want to enable the ability for their okta client to initiate the login process rather than relying on the login button from our login page to their specific okta client. Okta supports this easily enough, but it has a
I've attached a picture of the configration options within Okta.
Initate Login URIissI've attached a picture of the configration options within Okta.