FastAPI OpenIdConnect
Hey folks, I am trying to make the following to work:
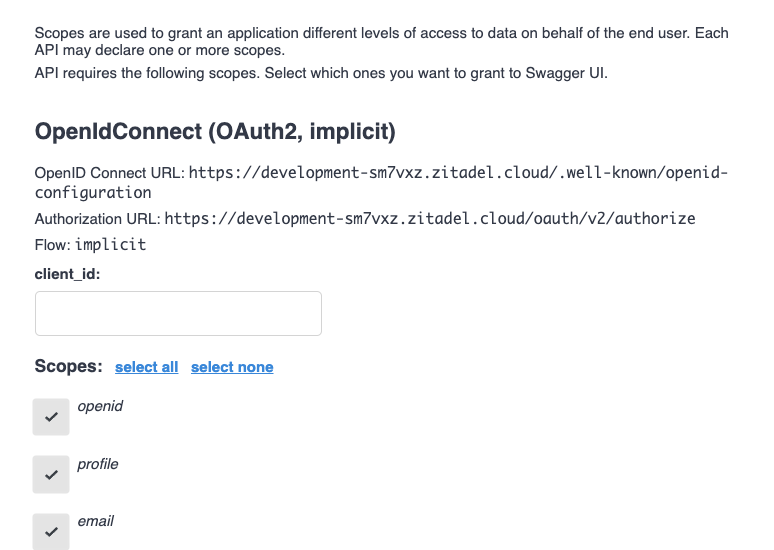
Then I visit the docs and try to use "OpenIdConnect (OAuth2, implicit)" mode, but I keep getting the following issue:
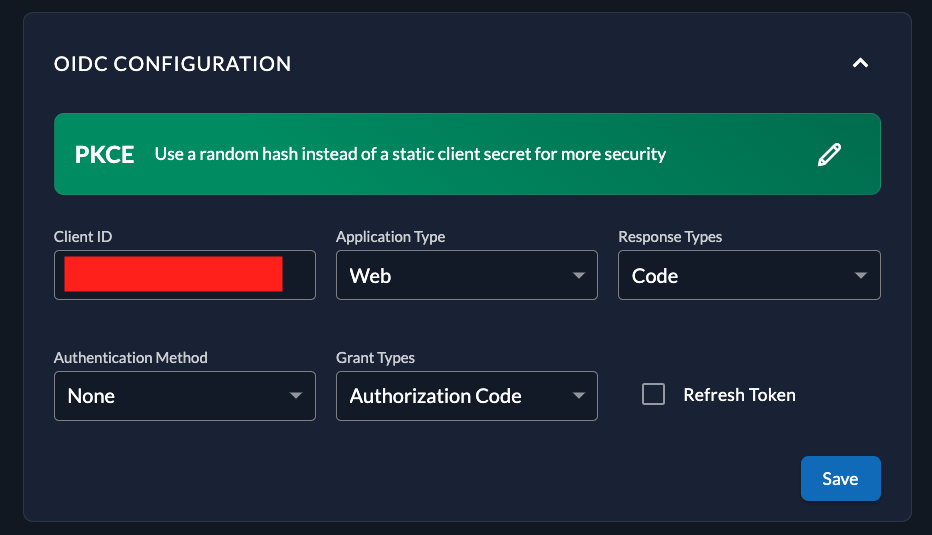
See the screenshots, I am not sure what else to try by now, I tried multiple combinations of response type, grant types (with implicit and not) ... I am just not sure what else to try by now and who is in fault here
Then I visit the docs and try to use "OpenIdConnect (OAuth2, implicit)" mode, but I keep getting the following issue:
See the screenshots, I am not sure what else to try by now, I tried multiple combinations of response type, grant types (with implicit and not) ... I am just not sure what else to try by now and who is in fault here