Hello Team, One specific SAML is bugging us more than a WEEK
Hey Team,
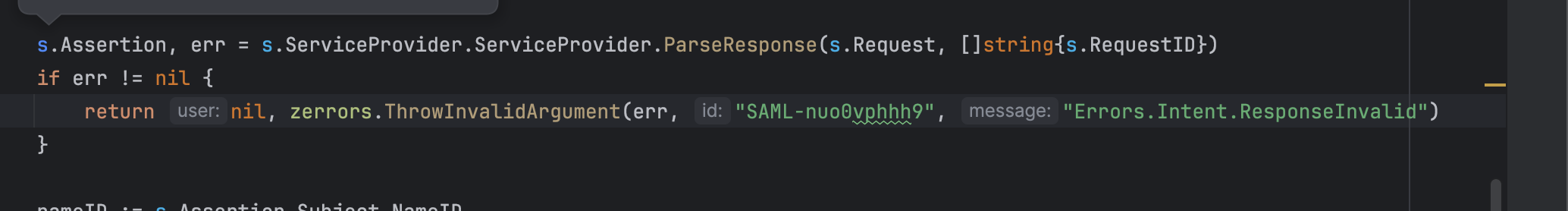
We've been working on integrating ADFS for a customer and encountered an unusual exception that's got us stumped. The error code is
Interestingly, when we attempted to reproduce the issue using our test ADFS server, everything worked fine, which was a bit disappointing However, the problem persists in the customer's environment. We've compared the decrypted assertions between our ADFS response and the customer's, but nothing stood out. We'd really appreciate any insights or help you could offer. Thanks a lot!
However, the problem persists in the customer's environment. We've compared the decrypted assertions between our ADFS response and the customer's, but nothing stood out. We'd really appreciate any insights or help you could offer. Thanks a lot!
We've been working on integrating ADFS for a customer and encountered an unusual exception that's got us stumped. The error code is
SAML-nuo0vphhh9Interestingly, when we attempted to reproduce the issue using our test ADFS server, everything worked fine, which was a bit disappointing
 However, the problem persists in the customer's environment. We've compared the decrypted assertions between our ADFS response and the customer's, but nothing stood out. We'd really appreciate any insights or help you could offer. Thanks a lot!
However, the problem persists in the customer's environment. We've compared the decrypted assertions between our ADFS response and the customer's, but nothing stood out. We'd really appreciate any insights or help you could offer. Thanks a lot!