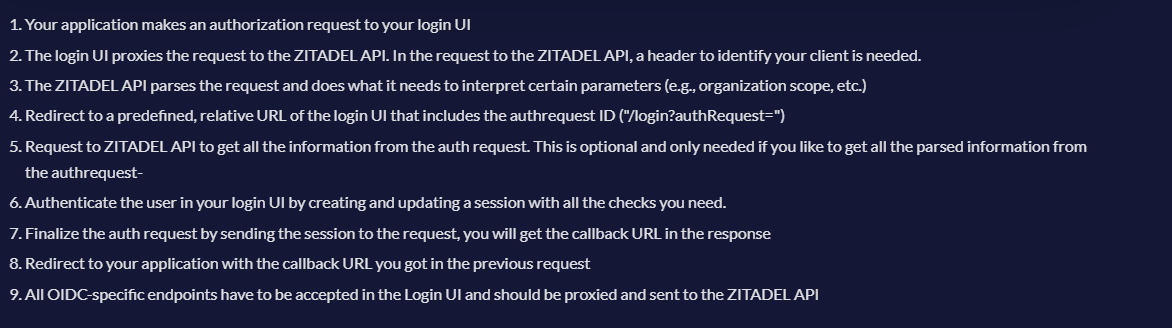
Custom Login UI - OIDC Support
I'm trying to build custom login UI supporting OIDC standard and I don't understand step 2 to step 4 from the picture I attached:
Redirect to a predefined, relative URL of the login UI that includes the authrequest ID ("/login?authRequest="
Where I need to predefine the URL?
Currently I'm using postman to test things, so step 2 is executed in postman. Is there some header param I need to add so Zitadel will know where to redirect?
In step 2, do I need to redirect to ZITADEL from browser or I can do that from the server side?
Redirect to a predefined, relative URL of the login UI that includes the authrequest ID ("/login?authRequest="
Where I need to predefine the URL?
Currently I'm using postman to test things, so step 2 is executed in postman. Is there some header param I need to add so Zitadel will know where to redirect?
In step 2, do I need to redirect to ZITADEL from browser or I can do that from the server side?